CISSP Videos
Language: English | Size:28.16 GB
Genre:eLearning
Files Included :
BCP DRP Core Concepts 1.mp4 (59.07 MB)
MP4
BCPDRP Core Concepts 2.mp4 (48.24 MB)
MP4
Choose the Best Answer Part 1.mp4 (64.33 MB)
MP4
Choose the Best Answer Part 2.mp4 (57.05 MB)
MP4
Data Classification Practice Question.mp4 (22.22 MB)
MP4
Domain 1 - Introduction.mp4 (1.52 MB)
MP4
Domain 1 - Security and Risk Management RPO, RTO, WRT, MTD.mp4 (12.09 MB)
MP4
Fujifilm Ransomware BCP DRP Correlation Part 1.mp4 (36.97 MB)
MP4
Fujifilm Ransomware BCP DRP Correlation Part 2.mp4 (22.21 MB)
MP4
Fujifilm Ransomware BCP DRP Correlation Part 3.mp4 (48.52 MB)
MP4
Practice Question Recovery Strategy.mp4 (67.13 MB)
MP4
Practice Question Review Video - Code of Ethics.mp4 (37.4 MB)
MP4
Practice Question Review Video Technical Preventative Control.mp4 (13.49 MB)
MP4
Practice Question Video Cloud Vendor Violations Tokenization.mp4 (66.34 MB)
MP4
Practice Question Video Privacy Impact Assessment.mp4 (89.55 MB)
MP4
Reverse Practice Question Review Video - States of Data.mp4 (30.02 MB)
MP4
Security and Risk Management Phase 1 of BCP DRP Scope and Initiation.mp4 (42.52 MB)
MP4
Security and Risk Management Phase 3 of BCP DRP Recovery Strategies.mp4 (32.08 MB)
MP4
Security and Risk Management Phase 2 of BCP DRP Business Impact Analysis.mp4 (43.45 MB)
MP4
Security and Risk Management Phase 4 and Phase 5 Testing and Maintenance.mp4 (27.72 MB)
MP4
Security and Risk Management The Importance of BCP DRP.mp4 (27.95 MB)
MP4
The CIA Triad.mp4 (23.83 MB)
MP4
The ISC2 CISSP Code of Ethics.mp4 (20.46 MB)
MP4
Administrative Controls 6-Subcategories of Controls.mp4 (27.69 MB)
MP4
Asset Classification Labels.mp4 (10.37 MB)
MP4
Baselines, Scoping, Tailoring, Standards.mp4 (72.8 MB)
MP4
Classification Labels Defined.mp4 (18.17 MB)
MP4
Cross-Domain Correlation Breach Attack Simulation Part 6.mp4 (90.9 MB)
MP4
Cross-Domain Correlation Just-In-Time Access Part 5.mp4 (55.47 MB)
MP4
Cross-Domain Correlation Kerberos Exploitation Part 2.mp4 (34.03 MB)
MP4
Cross-Domain Correlation Kerberos Exploitation Part 3.mp4 (70.73 MB)
MP4
Cross-Domain Correlation Li-Fi Part 4.mp4 (83.67 MB)
MP4
Cross-Domain Correlation Security Orchestration, Automation, and Response Part 8.mp4 (79.99 MB)
MP4
Cross-Domain Correlation Understand Requirements for Investigation Types Part 1.mp4 (57.53 MB)
MP4
Cross-Domain Correlation User and Entity Behavior Analytics Part 7.mp4 (56.65 MB)
MP4
Defense-in-Depth.mp4 (10.34 MB)
MP4
Equifax Breach Security Controls.mp4 (40.94 MB)
MP4
Introduction.mp4 (1.03 MB)
MP4
Physical Controls 6-Subcategories of Controls.mp4 (27.57 MB)
MP4
Practice Question Video Roles and Responsibilities.mp4 (79.57 MB)
MP4
Protecting Privacy.mp4 (21.19 MB)
MP4
Technical Controls 6-Subcategories of Controls.mp4 (52.03 MB)
MP4
Transparency, Concealment, Privacy, Secrecy.mp4 (56.68 MB)
MP4
Attacks on Cryptography Ciphertext-Only Attack.mp4 (34.75 MB)
MP4
Attacks on Cryptography Known-Plaintext Attack.mp4 (31.82 MB)
MP4
CISSP Practice Question Password Policy.mp4 (39.72 MB)
MP4
Common Criteria.mp4 (89.92 MB)
MP4
Community Hybrid Cloud.mp4 (19.94 MB)
MP4
Cross-Domain Correlation DES and a Broken Algorithm.mp4 (44.33 MB)
MP4
Diffie-Hellman Part 1.mp4 (26.8 MB)
MP4
Diffie-Hellman Part 2.mp4 (53.32 MB)
MP4
Digital Signatures.mp4 (64.08 MB)
MP4
Dual-Control.mp4 (15.3 MB)
MP4
Internet of Things Part 1-1 Introduction Types of Devices.mp4 (31.97 MB)
MP4
Internet of Things Part 1-2 How It Works.mp4 (31.97 MB)
MP4
Internet of Things Part 2-1 Top 10 IoT Security Vulnerabilities Countermeasures.mp4 (29.56 MB)
MP4
Internet of Things Part 2-2 Example of IoT Attack Core IoT CISSP Concepts.mp4 (31.5 MB)
MP4
Introduction Video.mp4 (1.53 MB)
MP4
Practice Question Best Evaluation Method.mp4 (16.28 MB)
MP4
Practice Question Clark-Wilson vs Biba Model.mp4 (8.49 MB)
MP4
Practice Question Internet of Things.mp4 (59.26 MB)
MP4
Practice Question MD2 Hashing Algorithm.mp4 (12.62 MB)
MP4
Private Cloud.mp4 (11.48 MB)
MP4
Public Cloud.mp4 (22.36 MB)
MP4
Public Key Infrastructure Part 1.mp4 (39.07 MB)
MP4
Public Key Infrastructure Part 2.mp4 (40.76 MB)
MP4
Quantum Cryptography.mp4 (40.04 MB)
MP4
Split-Knowledge.mp4 (20.53 MB)
MP4
Symmetric Key Encryption.mp4 (17.08 MB)
MP4
Vigenere Cipher.mp4 (29.83 MB)
MP4
Water Suppression Systems.mp4 (61.54 MB)
MP4
What is SCADA Part 1.mp4 (30.11 MB)
MP4
What is SCADA Part 2.mp4 (29.51 MB)
MP4
What is SCADA Part 3.mp4 (40.19 MB)
MP4
What is SCADA Part 4.mp4 (54.3 MB)
MP4
Why We Need Cryptography Part 1.mp4 (81.48 MB)
MP4
Why We Need Cryptography Part 2.mp4 (40.55 MB)
MP4
Basic Network Security.mp4 (35.58 MB)
MP4
Circuit vs Application Proxies Part 1.mp4 (14.17 MB)
MP4
Circuit vs Application Proxies Part 2.mp4 (19.73 MB)
MP4
Cross-Domain Correlation IPSec.mp4 (48.96 MB)
MP4
Cross-Domain Correlation Network Attacks Part 1.mp4 (44.25 MB)
MP4
Cross-Domain Correlation Network Attacks Part 2.mp4 (38.23 MB)
MP4
Cross-Domain Correlation Network Attacks Part 3.mp4 (47.7 MB)
MP4
Cross-Domain Correlation Network Attacks Part 4.mp4 (50.41 MB)
MP4
DDOS Countermeasures.mp4 (116.24 MB)
MP4
Difference Between DOS and DDOS.mp4 (13.08 MB)
MP4
Firewall Deployment Architectures Part 1.mp4 (38.48 MB)
MP4
Firewall Deployment Architectures Part 2.mp4 (37.96 MB)
MP4
Introduction.mp4 (1.42 MB)
MP4
Network Cabling.mp4 (26.56 MB)
MP4
Old OSI Model Video.mp4 (23.01 MB)
MP4
OSI Model Part 1.mp4 (26.9 MB)
MP4
OSI Model Part 2.mp4 (30.68 MB)
MP4
Packet vs Stateful Filter Firewalls.mp4 (41.11 MB)
MP4
Practice Question IPSec VPN.mp4 (13.17 MB)
MP4
Practice Question Network Collisions.mp4 (64.64 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 1.mp4 (24.43 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 10.mp4 (38.12 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 2.mp4 (36.65 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 3.mp4 (25.74 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 4.mp4 (34.18 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 5.mp4 (39.21 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 6.mp4 (43.58 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 7.mp4 (38.65 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 8.mp4 (28.15 MB)
MP4
Practice Question STP, OSPF, ICMP, BGP, GDPR 9.mp4 (28.15 MB)
MP4
Practice Question TLS Usage.mp4 (46.62 MB)
MP4
Practice Question VLANs.mp4 (82.32 MB)
MP4
Real World Demo of Port Address Translation (PAT).mp4 (36.61 MB)
MP4
Routers and Firewalls Part 1.mp4 (33.46 MB)
MP4
Routers and Firewalls Part 2.mp4 (35.36 MB)
MP4
Routers and Firewalls Part 3.mp4 (30.27 MB)
MP4
Routers and Firewalls Part 4.mp4 (19.4 MB)
MP4
Software Defined Networking.mp4 (42.23 MB)
MP4
Study Notes and Theory - A CISSP Study Guide (1).mp4 (34.96 MB)
MP4
Study Notes and Theory - A CISSP Study Guide.mp4 (38.12 MB)
MP4
The Concept of Network Security.mp4 (12.28 MB)
MP4
The TCP Handshake.mp4 (8.27 MB)
MP4
Transport Layer Security Part 1.mp4 (44.55 MB)
MP4
Transport Layer Security Part 2.mp4 (45.43 MB)
MP4
Attribute-Based Access Control.mp4 (49.9 MB)
MP4
Bell-LaPadula Model.mp4 (33.54 MB)
MP4
Biba Model.mp4 (40.01 MB)
MP4
Clark-Wilson Model.mp4 (65 MB)
MP4
Hard Token Implementation.mp4 (45.97 MB)
MP4
Introduction Video.mp4 (1.25 MB)
MP4
Kerberos.mp4 (71.4 MB)
MP4
Mandatory Access Control.mp4 (33.77 MB)
MP4
Need-to-Know Least Privilege.mp4 (36.6 MB)
MP4
OAuth.mp4 (48.46 MB)
MP4
OpenID.mp4 (46.23 MB)
MP4
Practice Question Federated Identity.mp4 (13.38 MB)
MP4
Real World Demo of OAuth and OpenID.mp4 (29.82 MB)
MP4
SAML Part 1.mp4 (34.07 MB)
MP4
SAML Part 2.mp4 (36.73 MB)
MP4
SAML.mp4 (35.31 MB)
MP4
Separation of Duties.mp4 (43.82 MB)
MP4
SPML.mp4 (14.2 MB)
MP4
Study Notes and Theory - A CISSP Study Guide.mp4 (13.38 MB)
MP4
What is Federated Identity.mp4 (26.23 MB)
MP4
XACML and SPML.mp4 (26.3 MB)
MP4
Cross-Domain Correlation Vulnerability Testing.mp4 (73.92 MB)
MP4
Introduction.mp4 (704.25 KB)
MP4
Practice Question Assurance.mp4 (39.73 MB)
MP4
Practice Question Security Awareness.mp4 (14.86 MB)
MP4
Practice Question Security Testing.mp4 (41.98 MB)
MP4
Practice Question Video Interdependencies.mp4 (10.17 MB)
MP4
Reverse Practice Question Test Environment.mp4 (39.13 MB)
MP4
Service Organization Controls (SOC 1, SOC 2, SOC 3) Part 1.mp4 (35.7 MB)
MP4
Service Organization Controls (SOC 1, SOC 2, SOC 3) Part 2.mp4 (35.03 MB)
MP4
Service Organization Controls (SOC 1, SOC 2, SOC 3) Part 3.mp4 (32.59 MB)
MP4
Service Organization Controls (SOC 1, SOC 2, SOC 3) Part 4.mp4 (33.03 MB)
MP4
Testing the Security of Software.mp4 (21.65 MB)
MP4
5 Question Review.mp4 (30.23 MB)
MP4
Cross-Domain Correlation Data Backup Verification.mp4 (38.51 MB)
MP4
Cross-Domain Correlation Single Point of Failure.mp4 (86.29 MB)
MP4
IaaS, PaaS, SaaS.mp4 (21.64 MB)
MP4
Industrial Control Systems Information Security Continuous Monitoring Part 1.mp4 (74.47 MB)
MP4
Industrial Control Systems Information Security Continuous Monitoring Part 2.mp4 (70.31 MB)
MP4
Industrial Control Systems Information Security Continuous Monitoring Part 3.mp4 (46.81 MB)
MP4
Industrial Control Systems Information Security Continuous Monitoring Part 4.mp4 (76.99 MB)
MP4
Introduction.mp4 (1.9 MB)
MP4
Job Rotation.mp4 (18.76 MB)
MP4
Malware Incident Response Part 1 Preparation.mp4 (60.01 MB)
MP4
Malware Incident Response Part 2.mp4 (22.38 MB)
MP4
Malware Incident Response Part 3.mp4 (39.59 MB)
MP4
Malware Incident Response Part 4.mp4 (35.04 MB)
MP4
Mandatory Vacations.mp4 (9.46 MB)
MP4
Practice Question Cloud Characteristics.mp4 (21.71 MB)
MP4
Practice Question Due Care.mp4 (20.8 MB)
MP4
Practice Question Incident Response.mp4 (38.42 MB)
MP4
Real-World Example of IaaS, PaaS, SaaS.mp4 (58.11 MB)
MP4
Attacks on Software Security.mp4 (28.95 MB)
MP4
Covert Storage and Timing Channels.mp4 (50.65 MB)
MP4
Cross-Domain Correlation CMMI.mp4 (41.37 MB)
MP4
Introduction Video.mp4 (963.3 KB)
MP4
Practice Question Most Risk.mp4 (42.74 MB)
MP4
SDLC Why We Need It How To Secure It Part 2.mp4 (45.9 MB)
MP4
SDLC Why We Need It How To Secure It Part 1.mp4 (34.04 MB)
MP4
Security of APIs.mp4 (105.02 MB)
MP4
Software or Systems Development Life Cycle Part 1.mp4 (26.66 MB)
MP4
Software or Systems Development Life Cycle Part 2.mp4 (41.52 MB)
MP4
SQL Injection Demo.mp4 (14.51 MB)
MP4
Systems Development Life Cycle.mp4 (39.77 MB)
MP4
Techniques to Secure Software Development.mp4 (36.13 MB)
MP4
Testing the Security of Software.mp4 (21.65 MB)
MP4
Why We Need Software Development Security.mp4 (39.98 MB)
MP4
1-2 Months Before Your Exam Part 1.mp4 (40.45 MB)
MP4
1-2 Months Before Your Exam Part 2.mp4 (50.51 MB)
MP4
2021 CISSP Exam FAQs Part 1.mp4 (39.75 MB)
MP4
2021 CISSP Exam FAQs Part 2.mp4 (45.53 MB)
MP4
2021 CISSP Exam FAQs Part 3.mp4 (71.85 MB)
MP4
How To Think Like A Manager - Director s Cut - Part 1.mp4 (40.98 MB)
MP4
How To Think Like A Manager - Director s Cut - Part 2.mp4 (48.63 MB)
MP4
How To Think Like A Manager - Director s Cut - Part 3.mp4 (38.25 MB)
MP4
How To Think Like A Manager - Director s Cut - Part 4.mp4 (38.75 MB)
MP4
How To Think Like A Manager - Director s Cut - Part 5.mp4 (50.1 MB)
MP4
Webinar - How To Think Like A Manager for Domain 1 - Part 1.mp4 (71.85 MB)
MP4
Webinar - How To Think Like A Manager for Domain 1 - Part 2.mp4 (56.02 MB)
MP4
Webinar - How To Think Like A Manager for Domain 1 - Part 3.mp4 (57.32 MB)
MP4
1 - 1 1 Organizational and Professional Ethics.mp4 (332.76 MB)
MP4
10 - 6 1 Investigation Obectives and Requirements.mp4 (318.36 MB)
MP4
11 - 7 1 Governance Documents.mp4 (314.9 MB)
MP4
12 - 8 1 Business Continuity Planning.mp4 (279.37 MB)
MP4
13 - 8 2 Business Impact Analysis.mp4 (323.3 MB)
MP4
14 - 9 1 Personnel Policies and Agreements.mp4 (292.61 MB)
MP4
15 - 9 2 Personnel Security Practices.mp4 (348.43 MB)
MP4
16 - 10 1 Risk Management Concepts.mp4 (341.16 MB)
MP4
17 - 10 2 Risk Management Frameworks.mp4 (336.73 MB)
MP4
18 - 10 3 Risk Assessment.mp4 (410.57 MB)
MP4
19 - 10 4 Controls and Countermeasures.mp4 (326.58 MB)
MP4
2 - 2 1 Information Security Fundamentals.mp4 (321.85 MB)
MP4
20 - 11 1 Threat Actors and Attributes.mp4 (403.74 MB)
MP4
21 - 11 2 Threat Modeling.mp4 (289.53 MB)
MP4
22 - 11 3 Attack Vectors.mp4 (345.05 MB)
MP4
23 - 11 4 Threat Intelligence.mp4 (330.4 MB)
MP4
24 - 12 1 Supply Chain Risk Management.mp4 (288.61 MB)
MP4
25 - 13 1 SETA Principles and Practices.mp4 (407.77 MB)
MP4
26 - 13 2 Social Enginnering.mp4 (304.56 MB)
MP4
27 - 14 1 Asset Classification.mp4 (330.95 MB)
MP4
28 - 15 1 Data and Asset Handling.mp4 (262.57 MB)
MP4
29 - 16 1 Asset Management.mp4 (336.13 MB)
MP4
3 - 3 1 Strategic Alignment.mp4 (313.62 MB)
MP4
30 - 17 1 Data Collection and Retention.mp4 (365.86 MB)
MP4
31 - 17 2 Deletion and Destruction.mp4 (337.64 MB)
MP4
32 - 18 1 Asset Lifecycle - EOL.mp4 (293.41 MB)
MP4
33 - 19 1 Control Baselines, Tailoring, and Scoping.mp4 (227.65 MB)
MP4
34 - 19 2 Data Protection Methods.mp4 (289.3 MB)
MP4
35 - 20 1 Secure Design Principles.mp4 (334.11 MB)
MP4
36 - 21 1 Information Security Models.mp4 (355.81 MB)
MP4
37 - 22 1 Security Evaluation Criteria.mp4 (250.83 MB)
MP4
38 - 23 1 Information Systems Security Capabilities.mp4 (388.13 MB)
MP4
39 - 24 1 Traditional Systems Architectures.mp4 (276.6 MB)
MP4
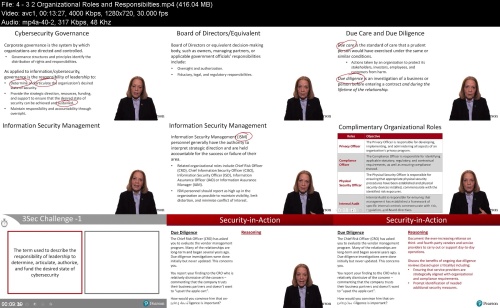
4 - 3 2 Organizational Roles and Responsibilties.mp4 (416.04 MB)
MP4
40 - 24 2 Database Systems.mp4 (284.57 MB)
MP4
41 - 24 3 Cloud-based Systems.mp4 (416 MB)
MP4
42 - 24 4 Embedded Systems.mp4 (291.1 MB)
MP4
43 - 24 5 IoT and IIoT.mp4 (279.25 MB)
MP4
44 - 24 6 Virtualized Systems.mp4 (312.03 MB)
MP4
45 - 24 7 Automation and Solution Elements.mp4 (323.94 MB)
MP4
46 - 25 1 Ciphers and Keys.mp4 (344.11 MB)
MP4
47 - 25 2 Symmetric Encryption.mp4 (355.98 MB)
MP4
48 - 25 3 Asymmetric Encryption.mp4 (389.57 MB)
MP4
49 - 25 4 Hashing and Digital Signatures.mp4 (389.65 MB)
MP4
5 - 3 3 Security Control Frameworks.mp4 (356.43 MB)
MP4
50 - 25 5 PKI and Digital Certificates.mp4 (363.76 MB)
MP4
51 - 25 6 Emerging Cryptography.mp4 (240.48 MB)
MP4
52 - 26 1 Cryptographic Attacks.mp4 (332.89 MB)
MP4
53 - 26 2 Hash and Kerberos Post-Exploitation Attacks.mp4 (307.19 MB)
MP4
54 - 26 3 Ransomware.mp4 (286.61 MB)
MP4
55 - 27 1 Physical Security Principles.mp4 (253.72 MB)
MP4
56 - 28 1 Site and Building Security.mp4 (342.59 MB)
MP4
57 - 28 2 Environmental Impact.mp4 (335.35 MB)
MP4
6 - 4 1 Regulatory and Contractual Obligations.mp4 (327.46 MB)
MP4
7 - 4 2 Privacy and Data Protection.mp4 (364.96 MB)
MP4
8 - 5 1 Cybercrime and Data Breaches.mp4 (311.76 MB)
MP4
9 - 5 2 Data Flow.mp4 (352.79 MB)
MP4
00 Course Overview.mp4 (3.24 MB)
MP4
00 Business Continuity Management Process.mp4 (9.54 MB)
MP4
01 Business Continuity Strategy.mp4 (8.88 MB)
MP4
02 Initial Planning.mp4 (10.69 MB)
MP4
00 Business Impact Analysis Part One.mp4 (8.59 MB)
MP4
01 Business Impact Analysis Part Two.mp4 (10.37 MB)
MP4
00 Create Contingency Strategies Part One.mp4 (6.56 MB)
MP4
01 Create Contingency Strategies Part Two.mp4 (10.12 MB)
MP4
02 Create Contingency Strategies Part Three.mp4 (8.35 MB)
MP4
00 Writing Business Continuity Plans Part One.mp4 (8.35 MB)
MP4
01 Writing Business Continuity Plans Part Two.mp4 (10.13 MB)
MP4
00 Implementing, Testing, and Maintaining Business Continuity Plans.mp4 (8.3 MB)
MP4
01 Maintaining Business Continuity Plans Part One.mp4 (7.37 MB)
MP4
02 Maintaining Business Continuity Plans Part Two.mp4 (6.76 MB)
MP4
00 Course Overview.mp4 (3.4 MB)
MP4
00 The People Problem.mp4 (8.07 MB)
MP4
01 Topics to Cover.mp4 (8.93 MB)
MP4
02 Malware and Ransomware.mp4 (5.65 MB)
MP4
03 Building a Team.mp4 (10.27 MB)
MP4
04 Training and Development.mp4 (4.9 MB)
MP4
05 Training.mp4 (7.01 MB)
MP4
00 Disciplinary Policy.mp4 (10.46 MB)
MP4
01 Employee Disciplinary Action.mp4 (5.46 MB)
MP4
02 Safety of Employees and Clients.mp4 (8.63 MB)
MP4
03 Criminal Activity.mp4 (7.27 MB)
MP4
00 Ethics and Culture.mp4 (8.25 MB)
MP4
00 Course Overview.mp4 (2.73 MB)
MP4
00 Risk Frameworks - ISO - IEC 27005, 31000, NIST, HTRA.mp4 (10.06 MB)
MP4
01 Risk Management Overview.mp4 (12.66 MB)
MP4
02 Risk Management Terminology.mp4 (9.48 MB)
MP4
03 Risk and Governance.mp4 (11.85 MB)
MP4
04 Risk Management Process Part 1.mp4 (8.44 MB)
MP4
05 Risk Management Process Part 2.mp4 (9.03 MB)
MP4
00 Framing Risk Part 1.mp4 (4.61 MB)
MP4
01 Framing Risk Part 2.mp4 (6.53 MB)
MP4
00 Assessing Risk.mp4 (12.56 MB)
MP4
01 Threat Modeling.mp4 (13.76 MB)
MP4
02 Risk Assessment Process Part 1.mp4 (9.71 MB)
MP4
03 Risk Assessment Process Part 2.mp4 (5.66 MB)
MP4
04 Risk Assessment Process Part 3.mp4 (11.61 MB)
MP4
05 Risk Assessment Results.mp4 (3.94 MB)
MP4
00 Mitigating Risk Part 1.mp4 (7.74 MB)
MP4
01 Mitigating Risk Part 2.mp4 (8.07 MB)
MP4
02 Mitigating Risk Part 3.mp4 (11.4 MB)
MP4
03 Mitigating Risk Part 4.mp4 (9.43 MB)
MP4
00 Monitoring Risk.mp4 (8.49 MB)
MP4
01 Risk Monitoring Process Part 1.mp4 (6.98 MB)
MP4
02 Risk Monitoring Process Part 2.mp4 (8.92 MB)
MP4
00 Course Overview.mp4 (2.93 MB)
MP4
00 Understanding Security Concepts.mp4 (6.89 MB)
MP4
01 Integrity and Availability.mp4 (6.73 MB)
MP4
02 Alignment with Business Mission.mp4 (9.6 MB)
MP4
03 Building a Security Program.mp4 (10.71 MB)
MP4
00 The Principles of Security Governance.mp4 (11.75 MB)
MP4
01 Security Related Laws and Regulations.mp4 (8.3 MB)
MP4
02 Types of Legal Systems.mp4 (5.47 MB)
MP4
00 Security Roles and Responsibilities.mp4 (10.74 MB)
MP4
01 Information Ownership.mp4 (14.84 MB)
MP4
00 Security Policies.mp4 (8.39 MB)
MP4
01 Implementing Security Policies.mp4 (10.1 MB)
MP4
00 Course Overview.mp4 (2.9 MB)
MP4
00 Information Classification.mp4 (4.29 MB)
MP4
01 Information Lifecycle Part 1.mp4 (8.35 MB)
MP4
02 Information Lifecycle Part 2.mp4 (7.96 MB)
MP4
00 Information Retention.mp4 (10.26 MB)
MP4
01 Information Deletion Part 1.mp4 (7.17 MB)
MP4
02 Information Deletion Part 2.mp4 (5.1 MB)
MP4
03 DLP and DRM.mp4 (8.77 MB)
MP4
00 Protection of Intellectual Property Part 1.mp4 (16.68 MB)
MP4
01 Protection of Intellectual Property Part 2.mp4 (8.07 MB)
MP4
02 Software Licensing.mp4 (12.02 MB)
MP4
00 Security Concerns During Divestitures and Aquisitions.mp4 (8.68 MB)
MP4
01 Mergers of Networks and Data.mp4 (10.79 MB)
MP4
00 Asset Management.mp4 (7.54 MB)
MP4
01 CMDB.mp4 (7.5 MB)
MP4
00 Course Overview.mp4 (2.61 MB)
MP4
00 History Part One.mp4 (11.31 MB)
MP4
01 History Part Two.mp4 (10.05 MB)
MP4
02 History Part Three.mp4 (10.08 MB)
MP4
03 Principles and Principals in Cryptography.mp4 (12.22 MB)
MP4
04 Cryptography Operations Part One.mp4 (11.03 MB)
MP4
05 Cryptography Operations Part Two.mp4 (9.29 MB)
MP4
06 Symmetric Algorithms Part One.mp4 (12.04 MB)
MP4
07 Symmetric Algorithms Part Two.mp4 (12.49 MB)
MP4
08 Symmetric Algorithms Part Three.mp4 (5.35 MB)
MP4
00 Digital Signatures Part One.mp4 (9.66 MB)
MP4
01 Key Management Part Two.mp4 (11.74 MB)
MP4
02 Digital Signatures Part Two.mp4 (12.22 MB)
MP4
03 Digital Signatures Part Three.mp4 (7.59 MB)
MP4
04 Key Management Part One.mp4 (7.83 MB)
MP4
00 Cryptanalytic Attacks Part One.mp4 (6.8 MB)
MP4
01 Cryptanalytic Attacks Part Two.mp4 (6.25 MB)
MP4
02 Implementation and Use of Cryptography Part One.mp4 (12.06 MB)
MP4
03 Implementation and Use of Cryptography Part Two.mp4 (7.73 MB)
MP4
04 Implementation and Use of Cryptography Part Three.mp4 (14.55 MB)
MP4
00 Course Overview.mp4 (2.79 MB)
MP4
00 Concepts Part One.mp4 (12.58 MB)
MP4
01 Concepts Part Two.mp4 (11.66 MB)
MP4
02 Bell-LaPadula Confidentiality Model.mp4 (12.51 MB)
MP4
03 Biba Integrity Model.mp4 (10.48 MB)
MP4
04 Other Security Models Part One.mp4 (9.16 MB)
MP4
05 Other Security Models Part Two.mp4 (10.68 MB)
MP4
00 Course Overview.mp4 (2.66 MB)
MP4
00 Open Systems Interconnect (OSI).mp4 (16.9 MB)
MP4
01 TCP - IP Model.mp4 (5 MB)
MP4
02 Physical Layer Part One.mp4 (9.01 MB)
MP4
03 Physical Layer Part Two.mp4 (7.07 MB)
MP4
04 Physical Layer Part Three.mp4 (8.56 MB)
MP4
05 Network and Transport Layers Part One.mp4 (8.36 MB)
MP4
06 Network and Transport Layers Part Two.mp4 (8.3 MB)
MP4
07 OSI Session, Presentation, Application Layers.mp4 (8.58 MB)
MP4
00 Secure Network Communications.mp4 (10.88 MB)
MP4
01 Protocol Selection Part One.mp4 (8.36 MB)
MP4
02 Protocol Selection Part Two.mp4 (5.27 MB)
MP4
03 Protocol Selection Part Three.mp4 (7.84 MB)
MP4
04 Network Encryption Part One.mp4 (6.33 MB)
MP4
05 Network Encryption Part Two.mp4 (8.8 MB)
MP4
06 IPSec and Link Layer Encryption Part One.mp4 (13.08 MB)
MP4
07 IPSec and Link Layer Encryption Part Two.mp4 (7.96 MB)
MP4
08 QoS, CoS and Wireless.mp4 (8.97 MB)
MP4
00 Network Attacks Part One.mp4 (10.16 MB)
MP4
01 Network Attacks Part Two.mp4 (6.71 MB)
MP4
02 Network Attacks Part Three.mp4 (10.17 MB)
MP4
03 Network Attacks Part Four.mp4 (11.62 MB)
MP4
04 Example of an Attack.mp4 (26.15 MB)
MP4
00 Course Overview.mp4 (2.78 MB)
MP4
00 The Evolution of Network Communications - Part One.mp4 (7.48 MB)
MP4
01 The Evolution of Network Communications - Part Two.mp4 (9.38 MB)
MP4
02 The Evolution of Network Communications - Part Three.mp4 (10.44 MB)
MP4
03 Network Connectivity - Part One.mp4 (8.33 MB)
MP4
04 Network Connectivity - Part Two.mp4 (8.91 MB)
MP4
05 Network Connectivity - Part Three.mp4 (8.79 MB)
MP4
06 Wide Area Networks.mp4 (8.15 MB)
MP4
07 Other Types of Networks.mp4 (9.61 MB)
MP4
00 Secure Network Configuration - Part One.mp4 (6.71 MB)
MP4
01 Secure Network Configuration - Part Two.mp4 (8.14 MB)
MP4
02 Wireless Network Security - Part One.mp4 (7.21 MB)
MP4
03 Wireless Network Security - Part Two.mp4 (6.17 MB)
MP4
04 Network Security Devices - Part One.mp4 (10.63 MB)
MP4
05 Netowrk Security Devices - Part Two.mp4 (8.85 MB)
MP4
06 Network Security Components - Part One.mp4 (7.16 MB)
MP4
07 Netowrk Security Components - Part Two.mp4 (8.93 MB)
MP4
00 Secure Network Operations.mp4 (6.72 MB)
MP4
01 Network Monitoring.mp4 (7.84 MB)
MP4
00 Course Overview.mp4 (3.28 MB)
MP4
00 Access Control Principles - Part One.mp4 (8.82 MB)
MP4
01 Access Control Principles - Part Two.mp4 (11.92 MB)
MP4
02 Layered Defense - Part One.mp4 (9.86 MB)
MP4
03 Layered Defense - Part Two.mp4 (4.83 MB)
MP4
04 Access Control Concepts - Part One.mp4 (10.66 MB)
MP4
05 Access Control Concepts - Part Two.mp4 (16.24 MB)
MP4
00 Access Controls Models.mp4 (12.04 MB)
MP4
01 Authentication - Part One.mp4 (10.12 MB)
MP4
02 Authentication - Part Two.mp4 (11.42 MB)
MP4
03 Authorization and Accounting.mp4 (7.32 MB)
MP4
00 CISA CISM CRISC CISSP.mp4 (13.86 MB)
MP4
01 Session Management - Part One.mp4 (7.53 MB)
MP4
02 Session Management - Part Two.mp4 (9.78 MB)
MP4
03 Access Control Management.mp4 (9.95 MB)
MP4
00 Course Overview.mp4 (2.65 MB)
MP4
00 Principles Part One.mp4 (10.07 MB)
MP4
01 Principles Part Two.mp4 (10.17 MB)
MP4
00 Building and Boundary Protection Part One.mp4 (10.28 MB)
MP4
01 Building and Boundary Protection Part Two.mp4 (7.76 MB)
MP4
02 Building and Boundary Protection Part Three.mp4 (8.6 MB)
MP4
03 Security of Sensitive Areas.mp4 (9.62 MB)
MP4
00 Fire Prevention, Detection, Suppression Part One.mp4 (11.61 MB)
MP4
01 Fire Prevention, Detection, Suppression Part Two.mp4 (8.44 MB)
MP4
02 Electrical Power.mp4 (13.51 MB)
MP4
00 Course Overview.mp4 (2.5 MB)
MP4
00 Security Control Assessment Introduction.mp4 (11.64 MB)
MP4
01 Testing and Assessment of Information and Information Systems - Part Two.mp4 (7.69 MB)
MP4
02 Testing and Assessment of Information and Information Systems - Part Three.mp4 (8.01 MB)
MP4
03 Testing and Assessment of Information and Information Systems - Part Four.mp4 (7.6 MB)
MP4
04 Log Management - Part One.mp4 (8.16 MB)
MP4
05 Log Management - Part Two.mp4 (9.6 MB)
MP4
06 Honey Nets.mp4 (8.45 MB)
MP4
00 Penetration Testing - Part One.mp4 (8.02 MB)
MP4
01 Penetration Testing - Part Two.mp4 (9.76 MB)
MP4
02 Penetration Testing - Part Three.mp4 (9.16 MB)
MP4
03 Vulnerability Assessment - Part One.mp4 (6.67 MB)
MP4
04 Vulnerability Assessment - Part Two.mp4 (6.96 MB)
MP4
05 Penetration Testing - Part Four.mp4 (8.66 MB)
MP4
06 Penetration Testing - Part Five.mp4 (7.34 MB)
MP4
07 Conducting a Penetration Test.mp4 (11.14 MB)
MP4
08 Other Test Areas - Part One.mp4 (12.54 MB)
MP4
09 Other Test Areas - Part Two.mp4 (12.61 MB)
MP4
00 Audit and Reporting - Part One.mp4 (8.7 MB)
MP4
01 Audit and Reporting - Part Two.mp4 (7.03 MB)
MP4
02 Assessment and Criteria - Part One.mp4 (7.25 MB)
MP4
03 Assessment and Criteria - Part Two.mp4 (10.05 MB)
MP4
00 Course Overview.mp4 (2.97 MB)
MP4
00 Risk and Controls.mp4 (11.19 MB)
MP4
01 Categories of Controls.mp4 (10.47 MB)
MP4
02 Types of Controls.mp4 (12.76 MB)
MP4
00 Control Selection Criteria Part 1.mp4 (4.55 MB)
MP4
01 Control Selection Criteria Part 2.mp4 (10.44 MB)
MP4
02 Additional Security Controls Part 1.mp4 (10.89 MB)
MP4
03 Additional Security Controls Part 2.mp4 (13.71 MB)
MP4
00 Course Overview.mp4 (2.98 MB)
MP4
00 Fundamentals.mp4 (8.85 MB)
MP4
01 Understanding Investigation.mp4 (10.69 MB)
MP4
02 Chain of Custody Contents.mp4 (9.87 MB)
MP4
00 Introduction to Incident Management Part One.mp4 (9.25 MB)
MP4
01 Introduction to Incident Management Part Two.mp4 (8.92 MB)
MP4
00 Incident Management Process Part One.mp4 (9.55 MB)
MP4
01 Incident Management Process Part Two.mp4 (10.75 MB)
MP4
02 Incident Management Process Part Three.mp4 (9.52 MB)
MP4
00 Course Overview.mp4 (2.26 MB)
MP4
00 Administration of Secure Information Systems - Part One.mp4 (8.9 MB)
MP4
01 Administration of Secure Information Systems - Part Two.mp4 (8.52 MB)
MP4
02 Security Operations Center - Part One.mp4 (10.18 MB)
MP4
03 Security Operations Center - Part Two.mp4 (8.43 MB)
MP4
04 Security Operations Center - Part Three.mp4 (5.92 MB)
MP4
05 Incident Management - Part One.mp4 (6.5 MB)
MP4
06 Incident Management - Part Two.mp4 (5.25 MB)
MP4
07 BCP - DRP - Part One.mp4 (9.7 MB)
MP4
08 BCP - DRP - Part Two.mp4 (5.93 MB)
MP4
09 BCP - DRP - Part Three.mp4 (8.01 MB)
MP4
00 Change Control and Secure Configuration - Part One.mp4 (8.69 MB)
MP4
01 Change Control and Secure Configuration - Part Two.mp4 (5.14 MB)
MP4
02 Change Control - Part One.mp4 (9.89 MB)
MP4
03 Change Control - Part Two.mp4 (12.3 MB)
MP4
04 Monitoring - Part One.mp4 (8.4 MB)
MP4
05 Monitoring - Part Two.mp4 (5.02 MB)
MP4
00 Backup and Media Management - Part One.mp4 (9.74 MB)
MP4
01 Backup and Media Management - Part Two.mp4 (9.13 MB)
MP4
02 Backup and Media Management - Part Three.mp4 (8.01 MB)
MP4
03 Media Management.mp4 (8.15 MB)
MP4
00 Course Overview.mp4 (2.59 MB)
MP4
00 Architecture Design.mp4 (9.7 MB)
MP4
01 Common Architectures Part One.mp4 (6.47 MB)
MP4
02 Common Architectures Part Two.mp4 (8.81 MB)
MP4
03 Cloud Architecture Part One.mp4 (14.17 MB)
MP4
04 Cloud Architecture Part Two.mp4 (6.27 MB)
MP4
05 Isolation and Memory Part One.mp4 (8.72 MB)
MP4
06 Isolation and Memory Part Two.mp4 (8.91 MB)
MP4
00 Architecture Items Part One.mp4 (14.42 MB)
MP4
01 Architecture Items Part Two.mp4 (13.31 MB)
MP4
02 Security Control Frameworks Part One.mp4 (13.46 MB)
MP4
03 Security Control Frameworks Part Two.mp4 (8.81 MB)
MP4
00 Course Overview.mp4 (2.5 MB)
MP4
00 Secure Software Design Part One.mp4 (9.01 MB)
MP4
01 Secure Software Design Part Two.mp4 (10.4 MB)
MP4
02 Secure Software Design Part Three.mp4 (7.03 MB)
MP4
03 Gathering (Security) Requirements Part One.mp4 (8.18 MB)
MP4
04 Gathering (Security) Requirements Part Two.mp4 (6.49 MB)
MP4
05 Software Project Planning Part One.mp4 (8.47 MB)
MP4
06 Software Project Planning Part Two.mp4 (8.86 MB)
MP4
07 Project Requirements Part One.mp4 (10.8 MB)
MP4
08 Project Requirements Part Two.mp4 (10.34 MB)
MP4
09 Project Requirements Part Three.mp4 (4.56 MB)
MP4
10 Project Design Part One.mp4 (8.47 MB)
MP4
11 Project Design Part Two.mp4 (6.67 MB)
MP4
12 Acquire and Implement.mp4 (10.56 MB)
MP4
00 Software Testing - Part One.mp4 (11.61 MB)
MP4
01 Software Testing - Part Two.mp4 (12.9 MB)
MP4
02 Software Testing - Part Three.mp4 (8.83 MB)
MP4
03 Secure Coding Practices - Part One.mp4 (11.23 MB)
MP4
04 Secure Coding Practices - Part Two.mp4 (12.9 MB)
MP4
05 Secure Coding Practices - Part Three.mp4 (6.85 MB)
MP4
06 Testing - Part One.mp4 (12.55 MB)
MP4
07 Testing - Part Two.mp4 (10.86 MB)
MP4
08 Deployment - Part One.mp4 (10.69 MB)
MP4
09 Deployment - Part Two.mp4 (5.97 MB)
MP4
10 Deployment - Part Three.mp4 (6.81 MB)
MP4
11 Operations - Part One.mp4 (5.93 MB)
MP4
12 Operations - Part Two.mp4 (9.26 MB)
MP4
00 Database Security Part One.mp4 (6.12 MB)
MP4
01 Database Security Part Two.mp4 (8.31 MB)
MP4
02 Database Structure Part One.mp4 (9.94 MB)
MP4
03 Database Structure Part Two.mp4 (9.89 MB)
MP4
04 Database Security Issues Part One.mp4 (7.49 MB)
MP4
05 Database Security Issues Part Two.mp4 (10.22 MB)
MP4
00 Course Overview.mp4 (2.26 MB)
MP4
00 The (ISC)2? Exam Format.mp4 (12.09 MB)
MP4
00 How to Prepare for an (ISC)2? Examination.mp4 (3.81 MB)
MP4
CISSP Videos.z01
CISSP Videos.z02
CISSP Videos.z03
CISSP Videos.z04
CISSP Videos.z05
CISSP Videos.z06
CISSP Videos.z07
CISSP Videos.z08
CISSP Videos.z09
CISSP Videos.z10
CISSP Videos.z11
CISSP Videos.z12
CISSP Videos.z13
CISSP Videos.z14
CISSP Videos.z15
CISSP Videos.z16
CISSP Videos.z17
CISSP Videos.z18
CISSP Videos.z19
CISSP Videos.z20
CISSP Videos.z21
CISSP Videos.z22
CISSP Videos.z23
CISSP Videos.z24
CISSP Videos.z25
CISSP Videos.z26
CISSP Videos.z27
CISSP Videos.z28
CISSP Videos.z29
CISSP Videos.z30
CISSP Videos.z31
CISSP Videos.z32
CISSP Videos.z33
CISSP Videos.z34
CISSP Videos.z35
CISSP Videos.z36
CISSP Videos.z37
CISSP Videos.z38
CISSP Videos.z39
CISSP Videos.z40
CISSP Videos.z41
CISSP Videos.z42
CISSP Videos.z43
CISSP Videos.z44
CISSP Videos.z45
CISSP Videos.z46
CISSP Videos.z47
CISSP Videos.z48
CISSP Videos.z49
CISSP Videos.z50
CISSP Videos.z51
CISSP Videos.z52
CISSP Videos.z53
CISSP Videos.z54
CISSP Videos.z55
CISSP Videos.z56
CISSP Videos.z57
CISSP Videos.zip
CISSP Videos.z01
CISSP Videos.z02
CISSP Videos.z03
CISSP Videos.z04
CISSP Videos.z05
CISSP Videos.z06
CISSP Videos.z07
CISSP Videos.z08
CISSP Videos.z09
CISSP Videos.z10
CISSP Videos.z11
CISSP Videos.z12
CISSP Videos.z13
CISSP Videos.z14
CISSP Videos.z15
CISSP Videos.z16
CISSP Videos.z17
CISSP Videos.z18
CISSP Videos.z19
CISSP Videos.z20
CISSP Videos.z21
CISSP Videos.z22
CISSP Videos.z23
CISSP Videos.z24
CISSP Videos.z25
CISSP Videos.z26
CISSP Videos.z27
CISSP Videos.z28
CISSP Videos.z29
CISSP Videos.z30
CISSP Videos.z31
CISSP Videos.z32
CISSP Videos.z33
CISSP Videos.z34
CISSP Videos.z35
CISSP Videos.z36
CISSP Videos.z37
CISSP Videos.z38
CISSP Videos.z39
CISSP Videos.z40
CISSP Videos.z41
CISSP Videos.z42
CISSP Videos.z43
CISSP Videos.z44
CISSP Videos.z45
CISSP Videos.z46
CISSP Videos.z47
CISSP Videos.z48
CISSP Videos.z49
CISSP Videos.z50
CISSP Videos.z51
CISSP Videos.z52
CISSP Videos.z53
CISSP Videos.z54
CISSP Videos.z55
CISSP Videos.z56
CISSP Videos.z57
CISSP Videos.zip

 Our Live Cams
Our Live Cams






 Reply With Quote
Reply With Quote